How to digitally sign PDF documents: Complete guide (2025)
Table of contents

- Use Nutrient SDKs to add secure, legally binding digital signatures across Web, iOS, Android, .NET, and server-side apps.
- Stay compliant with eIDAS (EU), ESIGN/UETA (US), and industry standards like FDA 21 CFR Part 11.
- Follow Nutrient best practices for certificate management, validation, and scalable server-side signing.
- Compare digital, electronic, and biometric signatures to pick the right fit for your workflow.
A digital signature works like an ink signature on paper, but it provides stronger security. PDF readers like Nutrient use this embedded data to verify two critical factors:
- Document integrity — no unauthorized modifications
- Author authenticity — confirmation of the signer’s identity
How the integrity of a PDF document is checked
If someone intercepts a PDF contract and changes its terms, digital signatures detect this tampering through hashing. A hash function converts document data into a fixed-size string. Any modification to the document produces a different hash value.
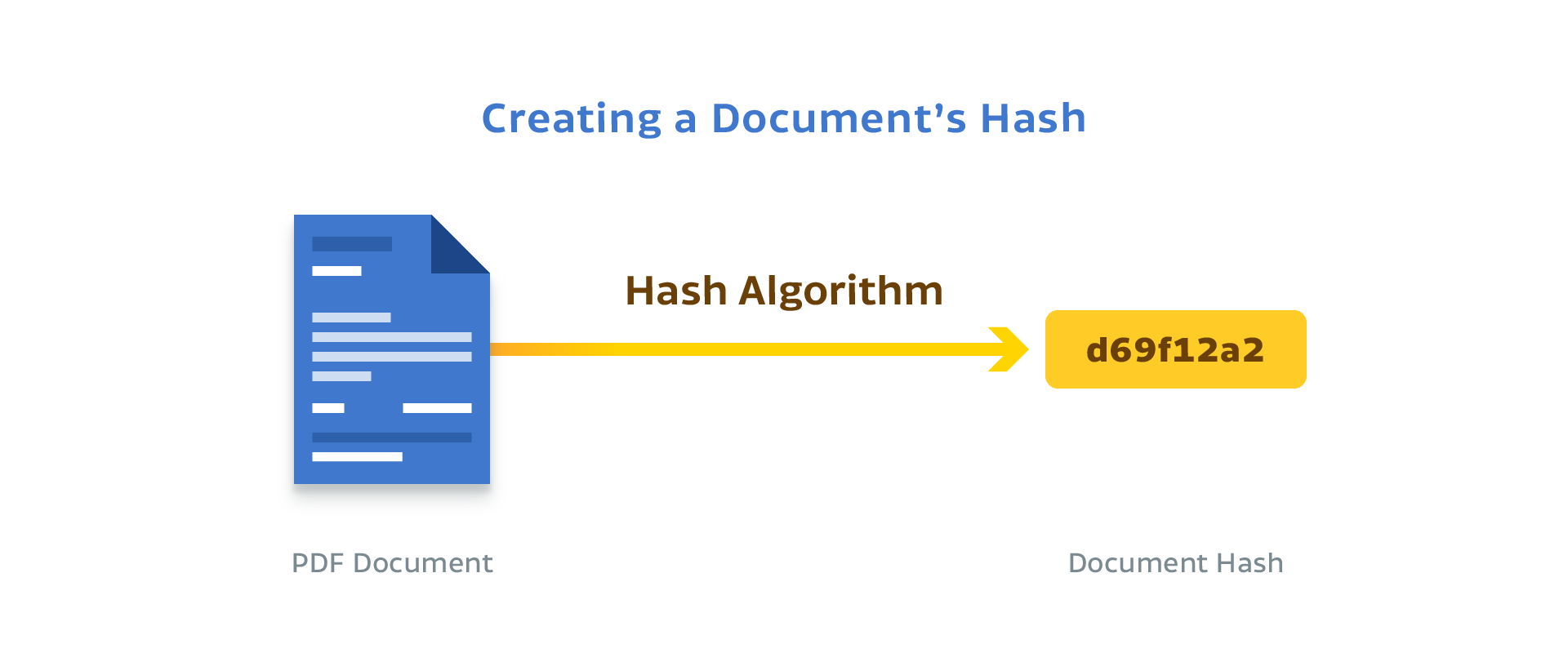
Signing a PDF applies a hash function to the document’s contents and stores the result. But hashing alone isn’t enough — an attacker could modify the document and recalculate the hash. Public-key cryptography prevents this by creating a tamper-proof digital signature of the hash.
Public-key cryptosystems
Traditional encryption requires both parties to share the same secret key beforehand — a security challenge in itself.
Public-key cryptography solves this. For digital signatures, the sender uses a private key to sign the message (or, more efficiently, a hash of it) and shares a public key with the receiver.
Two things must hold: (1) Only the sender controls the private key used to create the signature, and (2) anyone with the corresponding public key can verify that signature against the document’s hash. When these are true, the recipient can be confident the document came from the sender and hasn’t been altered.
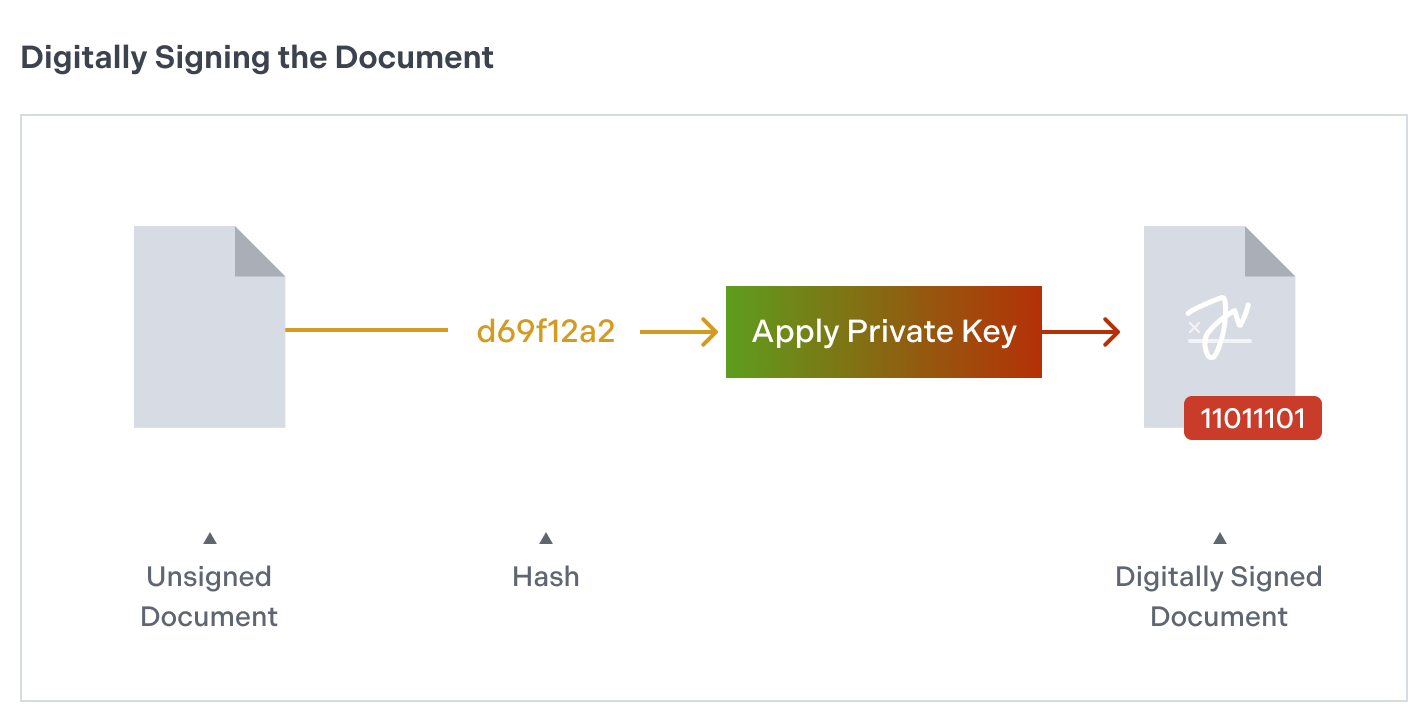
To be efficient without compromising security, Nutrient doesn’t digitally sign the entire PDF document; it signs a hash of it. When the recipient gets a signed document, they compute a fresh hash of the received content and use the sender’s public key to verify that the digital signature corresponds to that hash (i.e. that it was created with the matching private key).
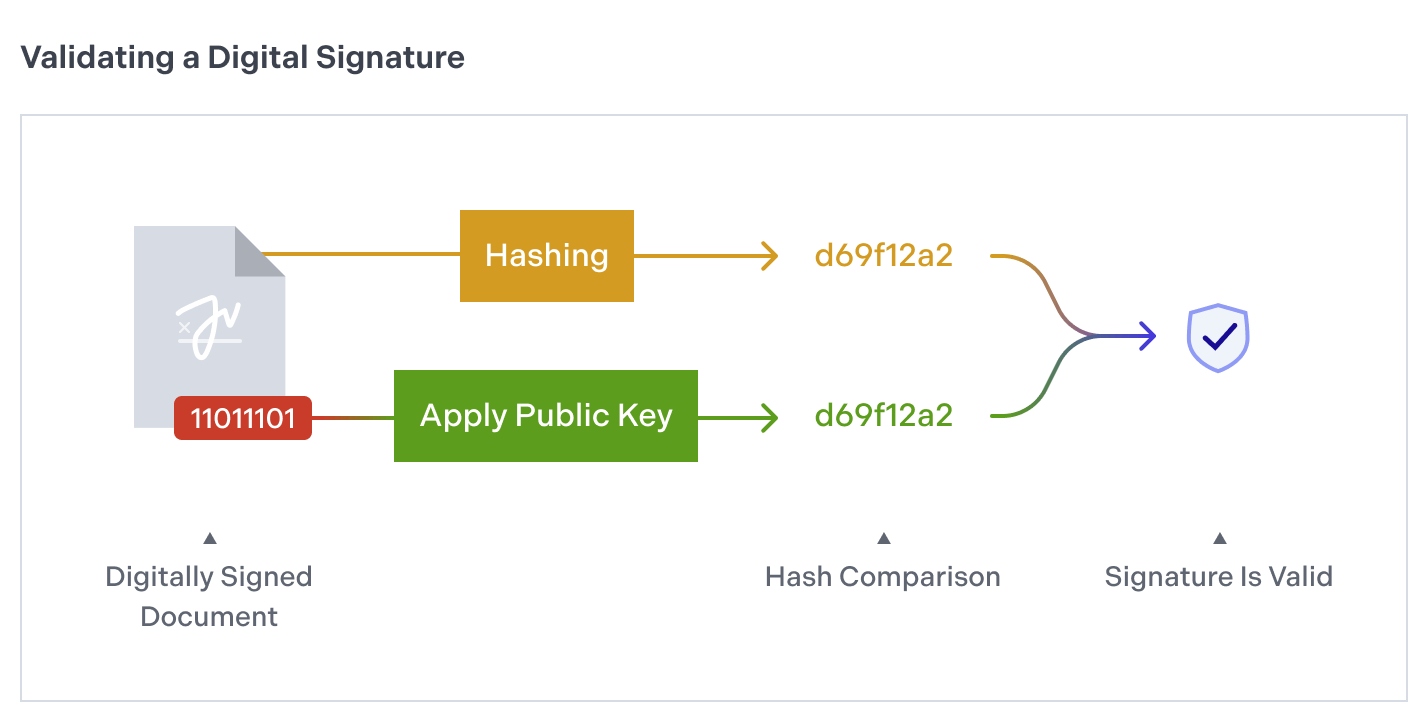
If the verification succeeds (the hashes match), the document hasn’t been modified and was created by you. This whole process is automatically supported by Nutrient, so you don’t need to perform these steps manually.
How to validate a digitally signed document with Nutrient
To validate a signed PDF with Nutrient using a set of trusted certificates, create an instance of a PDFSignatureValidator and initialize it with the SignatureFormElement you want to validate. Then call the verifySignature(withTrustedCertificates:) method, like this:
let signatureFormElement = unsignedDocument.annotationsForPage(at: 0, type: .widget)?.first { annotation -> Bool in return annotation is SignatureFormElement}let validator = PDFSignatureValidator(signatureFormElement: signatureFormElement)let certificates = try X509.certificates(fromPKCS7Data: certificateData)let signatureStatus = validator.verifySignature(withTrustedCertificates: certificates)The signatureStatus variable returns signature details: validity status, creation date, and other metadata.
How to sign a document with Nutrient iOS SDK
To sign a PDF, create a PKCS#12 keystore (PKCS12) that contains your private key and certificate. After that, initialize an instance of a PKCS12Signer with that keystore. Optionally, you can set a reason for the signature:
let keystore = PKCS12(data: p12data)let signer = PKCS12Signer(displayName: "Your name", pkcs12: keystore)signer.reason = "Contract agreement"Sign the document using the modern async API:
// Load the signing configuration.let configuration = SigningConfiguration(dataSigner: privateKey, certificates: certificates)
// Sign the document.try await document.sign(formElement: signatureFormElement, configuration: configuration, outputDataProvider: FileDataProvider(fileURL: outputURL))Display the signed document using a PDFViewController.
Additional resources from Nutrient documentation:
Cross-platform implementation
Digital signatures work across all major platforms. Each Nutrient SDK provides platform-specific optimizations and native integrations.
Web/JavaScript implementation
Nutrient Web SDK provides full support for digital signatures directly in the browser, powered by the Web Crypto API. This enables secure, standards-compliant signing without requiring external plugins or native applications.
You can implement client-side signing for decentralized workflows or connect to server-side signing services when centralized certificate management is required. The SDK is designed for seamless integration into existing web applications and workflows.
Key capabilities
- Browser-native cryptographic operations via Web Crypto API
- PKCS#12 certificate support for enterprise-grade signing
- Real-time signature validation to ensure authenticity and integrity
- Cross-browser compatibility with modern standards
- Flexible integration with both client-side and server-side workflows
Learn more
For implementation instructions, browser compatibility details, and security best practices, refer to our Web SDK digital signatures guide.
Android implementation
Nutrient Android SDK provides secure digital signature capabilities with deep integration into the Android platform. Signing workflows can leverage the Android Keystore system for certificate storage and private key access, as well as external providers for advanced security needs.
Key features
- Integration with Android Keystore via
MemorySignerandKeyStore.PrivateKeyEntry - Support for external signature providers, including hardware security modules (HSMs)
- Biometric signature data capture (e.g. pressure, timing, input method) for enhanced authenticity
- Full support for both Kotlin and Java SDKs
Implementation resources
.NET cross-platform support
Nutrient .NET SDK provides robust digital signature capabilities across desktop, mobile, and server environments. It runs cross-platform on Windows, macOS, and Linux, with support for modern .NET versions (6, 7, and 8) as well as .NET Framework where required.
Platform support
- .NET MAUI (Windows, macOS via Mac Catalyst, iOS, Android)
- WPF and WinForms desktop applications
- ASP.NET Core web applications
- Console and service applications
This breadth of support makes it possible to build secure signing workflows for everything from enterprise desktop apps to mobile solutions and server-side services.
Getting started
Refer to the .NET SDK documentation for platform-specific setup instructions, system compatibility details, and implementation patterns.
Server-side implementation
Server-side signing with Nutrient Document Engine centralizes certificate management and provides enterprise-grade security and scalability for digital signature workflows.
Enterprise benefits
- Centralized certificate storage and management for compliance and security
- Hardware security module (HSM) integration, including AWS CloudHSM and third-party providers
- Audit trail and compliance logging to meet regulatory requirements
- High-volume batch processing for large-scale document workflows
- API-based integration via Document Engine and the Digital Signatures API for seamless system connectivity
Learn more
- Server-side digital signatures guide
- Digital signature integrations overview
- Nutrient Processor API documentation
Implementation guidance: Each platform has unique considerations for certificate storage, security, and user experience. We recommend starting with our platform-specific getting started guides to understand the optimal approach for your target environment.
Legal compliance and regulatory frameworks
Digital signatures must meet specific legal and regulatory requirements, depending on your industry and jurisdiction, to be enforceable. Nutrient SDKs are designed to help you build compliant workflows across regions and sectors.
eIDAS Regulation (European Union)
The Electronic Identification, Authentication and Trust Services (eIDAS) regulation establishes the framework for electronic signatures in the EU:
Advanced Electronic Signatures (AdES)
- Uniquely linked to the signatory
- Capable of identifying the signatory
- Created using a secure signature creation device
- Detects any subsequent data changes
Qualified Electronic Signatures (QES)
- Highest assurance level under eIDAS
- Equivalent to handwritten signatures
- Requires qualified certificates
- Created with a qualified signature creation device
US electronic signature laws
ESIGN Act (federal)
The Electronic Signatures in Global and National Commerce (ESIGN) Act establishes the federal framework for electronic signatures:
- Intent to sign – Signer must demonstrate clear intent
- Consent to electronic records – Parties must agree to an electronic process
- Record retention – Signed records must remain accessible and reproducible
- Attribution – Signature must be attributable to a specific individual
UETA (state level)
The Uniform Electronic Transactions Act (UETA) complements ESIGN at the state level:
- Adopted by 48 US states
- Technologically neutral
- Requires authentication of signatures
- Emphasizes preservation of record integrity
Industry-specific requirements
FDA 21 CFR Part 11 (pharmaceutical)
The FDA’s 21 CFR Part 11 governs the use of electronic records and signatures in regulated industries:
Key requirements
- Multi-factor or biometric authentication
- Tamper-evident audit trails
- System validation and documentation
- Role-based access controls
- Ongoing security assessments
Financial services
Industries like banking and payments often require compliance with frameworks such as KYC, AML, Sarbanes-Oxley, and PCI DSS. These are common considerations for secure digital signature workflows.
Signature type comparison
Choosing the right signature type depends on security and compliance requirements:
Digital signatures
- Cryptographically secured
- Certificate-based authentication
- Tamper detection
- Non-repudiation
- Legally binding in most jurisdictions
Electronic signatures
- Image of handwritten signature
- Basic identity verification
- Limited tamper detection
- Suitable for low-risk documents
- Simple and user-friendly
Biometric signatures
- Captures signing behavior (pressure, speed, rhythm)
- Strong authentication
- High-security applications
- Requires specialized hardware
When to use each type
| Use case | Digital | Electronic | Biometric |
|---|---|---|---|
| Legal contracts | ✅ Recommended | ⚠️ Low-risk only | ✅ High-security |
| Financial documents | ✅ Required | ❌ Not sufficient | ✅ Premium option |
| Healthcare records | ✅ Compliant | ⚠️ Limited compliance | ✅ Full compliance |
| Internal approvals | ✅ Secure | ✅ Sufficient | ⚠️ Overkill |
| Consumer applications | ✅ Trusted | ✅ Easy to use | ❌ Complex |
Security best practices
Implementing digital signatures securely requires careful handling of certificates, keys, and validation processes. Nutrient SDKs and Document Engine provide built-in tools to support trusted, legally binding signature workflows, but correct setup and governance are essential.
Certificate management
Certificate lifecycle
Proper certificate management involves several phases, outlined below.
Generation and enrollment
- Create certificate signing requests (CSRs) with strong key pairs (RSA 2048+ or higher)
- Obtain certificates from a trusted Certificate Authority (CA), ideally AATL-backed for production use
- Install issued certificates with secure storage practices
Validation and monitoring
- Validate certificate chains against trusted root certificates
- Handle untrusted, expired, or self-signed certificates appropriately
- Provide a trusted root store (supported in Document Engine) for verification
- Use revocation checking (CRL or OCSP) as a best practice to ensure certificates haven’t been compromised
Renewal and rotation
- Renew certificates proactively before expiration
- Rotate keys regularly to mitigate long-term risk
- Deploy updates through controlled, auditable processes
Resources
Key storage security
- Hardware security modules (HSMs) — Supported through integrations such as AWS CloudHSM for high-assurance key storage
- Centralized key management — Available via the Document Engine for server-side signing and enterprise workflows
- Access controls — Use role-based permissions and audit logs for certificate and key usage
- Strong keys — Always use secure algorithms (RSA 2048+, ECDSA, or equivalent) for cryptographic operations
Security reminder: Always validate signatures against trusted certificate chains. For maximum assurance, implement certificate revocation checking (CRL/OCSP), even if it’s not explicitly required by your workflow.
Performance tip: To optimize large document workflows, Nutrient signs a hash of the PDF rather than the entire file. This approach significantly reduces processing time while maintaining full cryptographic integrity.
Resources
Conclusion
Digital signatures secure your PDFs against tampering and verify signer identity, making them essential for compliance and trust. With Nutrient’s cross-platform SDKs and server-side tools, you can implement legally binding signatures on Web, mobile, .NET, and enterprise systems.
Get started with Nutrient’s digital signature SDK and free trial to build secure, compliant workflows today.
Related security guides
- Dynamic document redaction
- PDF permissions vs. encryption
- What’s hiding in your PDF
- Electronic vs. digital signatures
Platform-specific signing
FAQ
A PDF digital signature is a cryptographically secure method of signing documents that ensures both document integrity (the content hasn’t been altered) and signer authenticity (confirming the signer’s identity). Unlike electronic signatures, digital signatures rely on public-key cryptography and digital certificates, creating legally binding, tamper-evident signatures.
Yes. Digital signatures are legally binding in most jurisdictions when they comply with applicable regulations:
- United States — Recognized under the ESIGN Act and UETA
- European Union — Equivalent to handwritten signatures under eIDAS regulation
- Other regions — Widely recognized when implemented with proper authentication and compliance measures
The legal validity depends on factors such as signer intent, consent to use electronic processes, and maintaining document integrity.
Digital signatures — Use cryptographic certificates for maximum security, tamper detection, and non-repudiation. Best for legal contracts and high-security documents.
Electronic signatures — Simple visual marks (typed name, image of a handwritten signature) with basic identity verification. Suitable for low-risk documents and user-friendly workflows.
Biometric signatures — Capture behavioral characteristics such as pressure, speed, and rhythm during signing. Provide strong authentication for high-security use cases but may require specialized hardware.
Nutrient provides SDKs and APIs for all major environments:
- Web/JavaScript — Browser-based signing with native cryptography (Web Crypto API)
- iOS — Native Swift implementation with certificate-based signing
- Android — Kotlin/Java support with Android Keystore integration
- .NET — Cross-platform support including .NET MAUI, WPF/WinForms, ASP.NET Core, and console apps
- Server-side — REST APIs for centralized signing, validation, and enterprise workflows
All SDKs support async/await patterns, error handling, and platform-specific optimizations.
Digital signatures can be configured to meet legal and regulatory frameworks, including:
- eIDAS (EU) — Advanced and Qualified Electronic Signatures (AdES/QES)
- ESIGN Act / UETA (US) — Federal and state-level validation of e-signatures
- FDA 21 CFR Part 11 (pharmaceutical) — Audit trails, access control, and eSignature linkage
Other frameworks, such as HIPAA (healthcare) and financial compliance standards (KYC, AML, Sarbanes-Oxley, PCI DSS), are common industry considerations.
Common issues and solutions:
Certificate problems — Ensure full certificate chains are included, check expiration dates, and validate against trusted root certificates.
Platform-specific issues — iOS certificate access, Android Keystore usage, and Web Crypto API compatibility.
Performance issues — For large documents, rely on hash-only signing (standard in Nutrient SDKs) and consider server-side processing for bulk operations.
Validation failures — Verify trusted certificate stores, timestamps, and document integrity preservation.
Key practices include:
- Certificates — Use trusted Certificate Authorities (CAs) and AATL-backed certificates for production.
- Key storage — Secure keys in HSMs or keystores, never in plain text.
- Validation — Validate certificate chains and, where required, implement revocation checking (CRL/OCSP).
- Audit trails — Maintain logs of signer identity, timestamps, and document hashes.
- Access controls — Enforce role-based permissions and multi-factor authentication for signing operations.
Yes. Nutrient supports high-volume server-side signing and validation with Document Engine and the Processor API:
- Server-side APIs — Handle large document volumes with centralized certificate management.
- Async operations — Prevent blocking and optimize throughput with async/await.
- Scalability — Scale across servers for enterprise workloads.
- Error handling — Implement retries and detailed logging for failed operations.
This is ideal for enterprise workflows such as contract renewals, compliance reporting, and automated approvals.
Costs depend on your deployment model and compliance needs:
- Licensing — Digital signature features are included in Nutrient SDK and API licensing.
- Certificates — Pricing varies by Certificate Authority and validation level (standard vs. qualified certificates).
- Infrastructure — Enterprise deployments may require server hosting, HSMs, and secure storage.
- Compliance — Additional costs may arise for audits, validation, and legal reviews.
For detailed pricing tailored to your needs, contact Nutrient.